TrustCloud Export
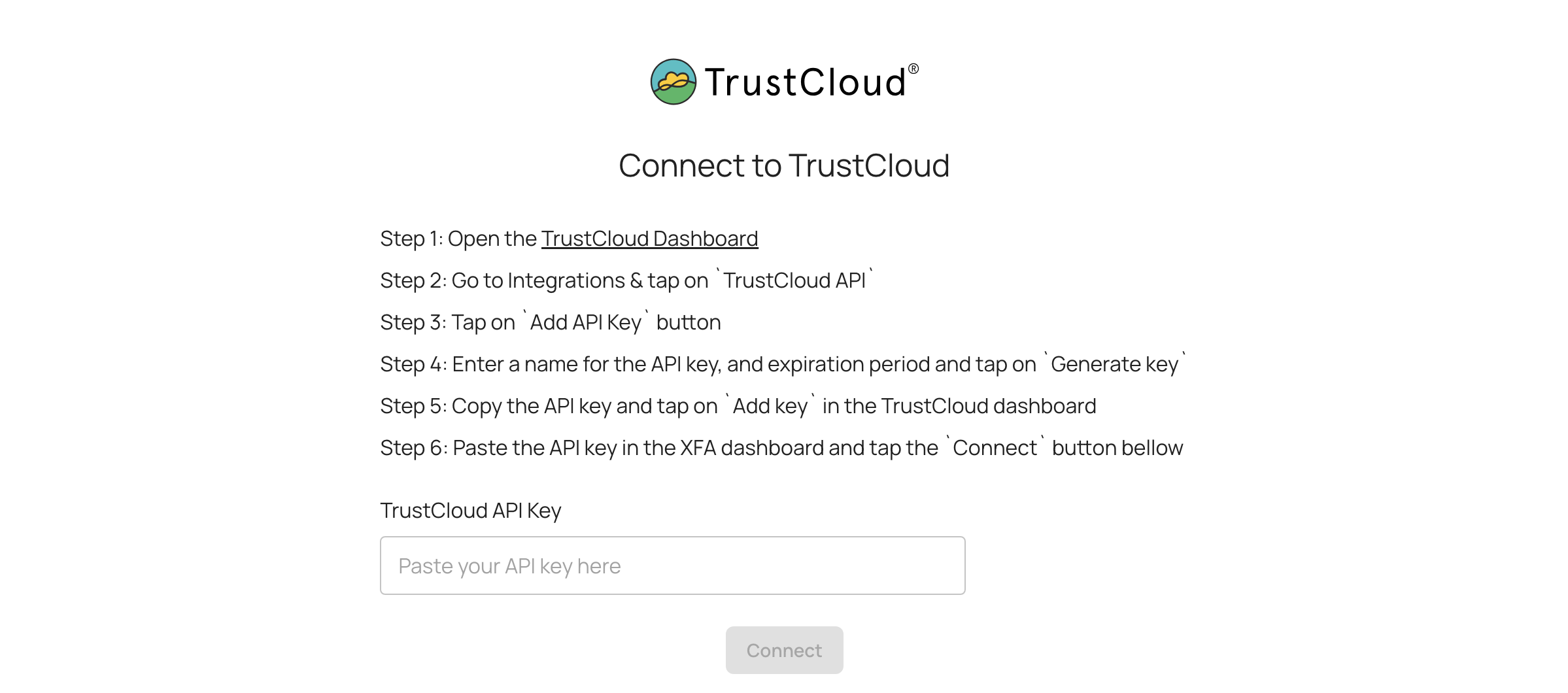
You can export your devices to TrustCloud to provide device security proof automatically for your compliance needs.
Get started in the TrustCloud Dashboard under Integrations.

You can export your devices to TrustCloud to provide device security proof automatically for your compliance needs.
Get started in the TrustCloud Dashboard under Integrations.
XFA can be used as a factor through the BYO MFA functionality in OneLogin. This allows XFA to be seamlessly added to any application from within the OneLogin admin dashboard, given that it uses Ping Identity as the identity provider.
When a user authenticates with Ping Identity, as an additional factor after supplying a username & password, the user is redirected to XFA to verify that the device is compliant with the device security policy before authenticating the user. This assures that only devices that comply with the security policy are allowed access.
Click here to get started in the XFA Dashboard.

We’re excited to share that XFA has enhanced its coverage on Linux operating systems, delivering even deeper protection, broader visibility, and faster response to any potential risks. Especially on the systems that are often left out (this one is for the techies).
We've released our new Desktop Application for macOS and Windows. This application will replace the web extension and provide a more seamless experience for users.
The XFA Desktop Application allows dekstop devices to communicate with the XFA service and serves as a critical tool for maintaining device compliance, managing multi-factor authentication (MFA), and controlling data sharing with organizations.
Note: Users can uninstall their browser extension, except for Brave users who should keep it installed.
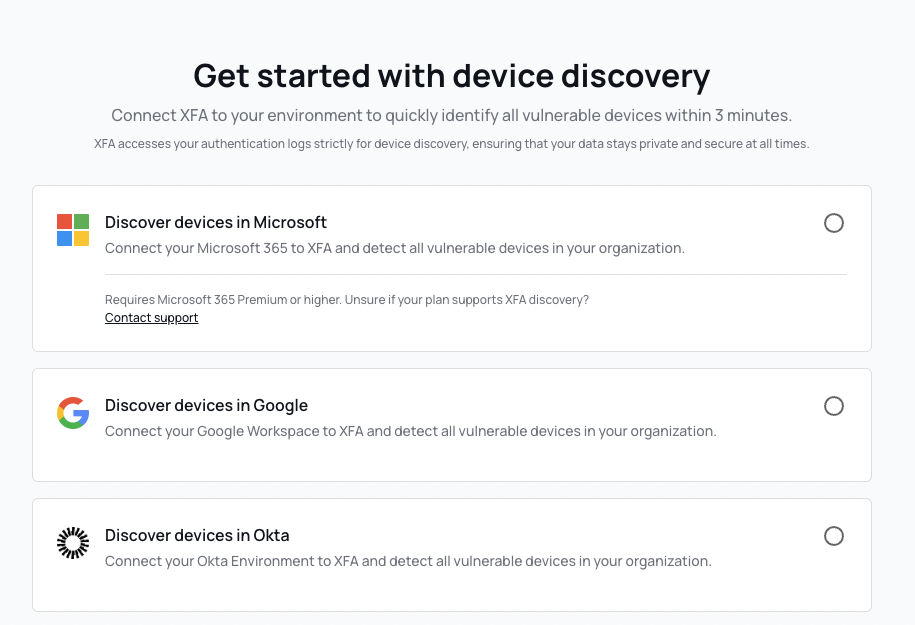
You can now link your Okta account to XFA to discover all your devices and ensure compliance. XFA reads authentication logs and derives the devices used by each user from these logs. This will lead to a full overview of all discovered devices without verified information.
Get started in the XFA Dashboard under Discovery.
XFA is now a Thoropass Partner!
You can use XFA to provide device security proof automatically for your compliance needs, pushing updates regularly to Thoropass.
Get started in the Thoropass Dashboard > Under settings click on 'Integrations' > Find 'XFA' > click 'Learn more' > click 'Set Up Integration' > click 'New Connection' > you'll be redirected to XFA to confirm your integration.

You can now link your Google Workspace or Microsoft Entra ID account to XFA to discover all your devices and ensure compliance. XFA reads authentication logs and derives the devices used by each user from these logs. This will lead to a full overview of all discovered devices without verified information.
Get started in the XFA Dashboard under Discovery.
You can export your devices to Vanta to provide device security proof automatically for your compliance needs.
Get started in the Vanta Dashboard under Integrations.
XFA can be used as a factor through the BYO MFA functionality in OneLogin. This allows XFA to be seamlessly added to any application from within the OneLogin admin dashboard, given that it uses OneLogin as the identity provider.
When a user authenticates with OneLogin, as an additional factor after supplying a username & password, the user is redirected to XFA to verify that the device is compliant with the device security policy before authenticating the user. This assures that only devices that comply with the security policy are allowed access.
XFA can be used as a factor through the External Authentication Methods functionality in Microsoft EntraID. This allows XFA to be seamlessly added to any application from within the Microsoft EntraID admin dashboard, given that it uses EntraID as the identity provider.
When a user authenticates with EntraID, as an additional factor after supplying a username & password, the user is redirected to XFA to verify that the device is compliant with the device security policy before authenticating the user. This assures that only devices that comply with the security policy are allowed access.