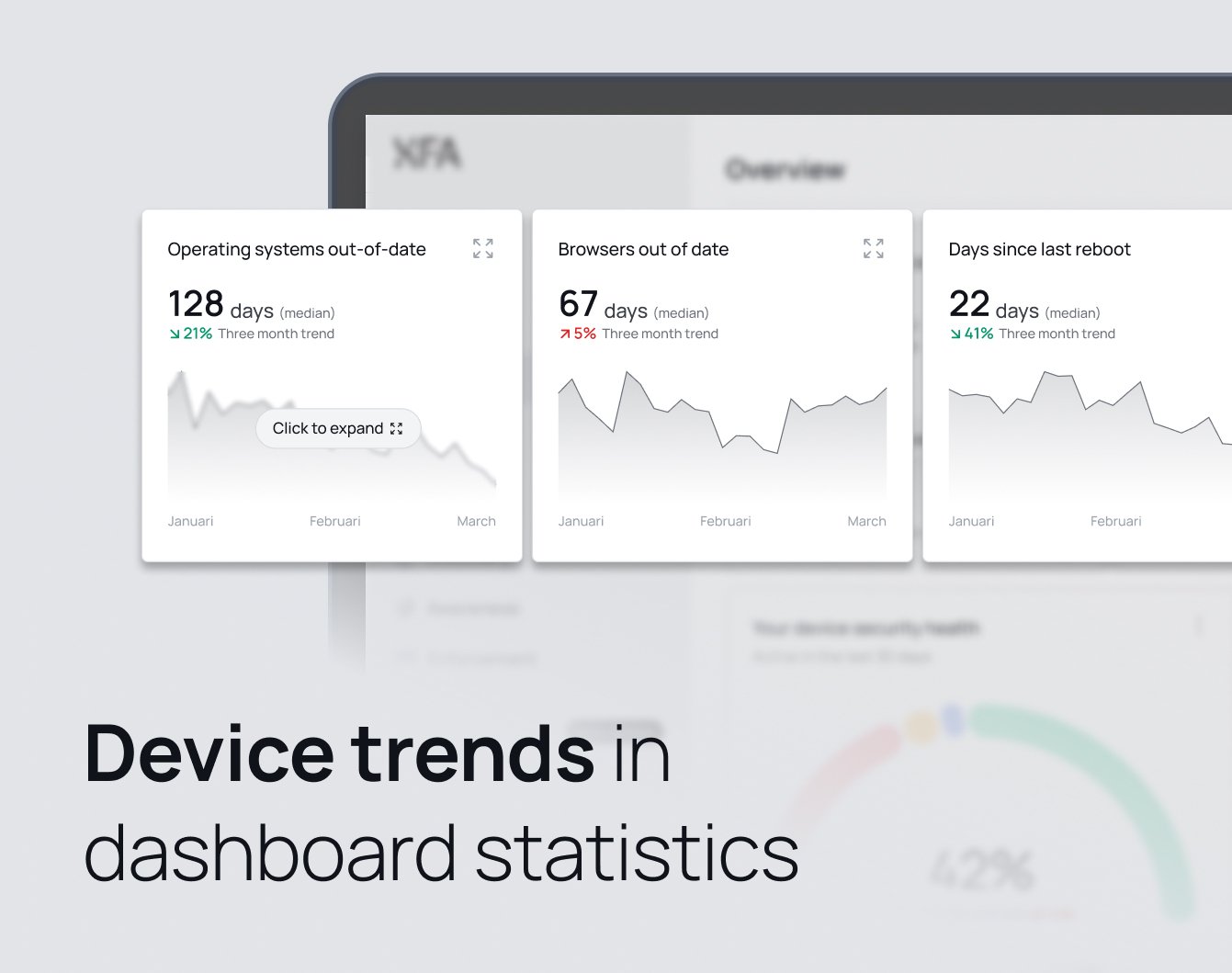
We're excited to announce that XFA now includes Trends functionality in the dashboard, allowing administrators to track device security improvements and deteriorations over time.
The new trends feature provides valuable insights into your organization's security posture by displaying historical data and patterns. You can now visualize how your device fleet's compliance has evolved, making it easier to identify security trends and take proactive measures.
Current Features
Currently, you can view trends for:
- OS Out of Date: Track how many devices have outdated operating systems over time
Coming Soon
We're actively working on expanding the trends functionality to include more comprehensive statistics, giving you deeper insights into:
- Days since last reboot compliance
- Device encryption compliance
- Browser security status
- And many more security metrics
Get Started
You can explore the new trends feature today by visiting the dashboard. This powerful addition to the XFA dashboard helps you make data-driven decisions about your organization's security policies and understand the impact of your security initiatives over time.
Stay tuned for more trend categories coming soon!